Site 2 Site VPN pfSense to Azure Stack
Today I want you to show how to build up a Site2Site VPN Tunnel from my HomeOffice to Azure Stack! I thought that must be an easy way, because i am well equipped at home. Well, during the setup I learned a lot about IPSec and what my local firewall can manage and what not ;(
You need a firewall that supports IKEv2!!
So i had a Sophos UTM 9.5 firewall at home which is NOT compatible and not supporting IKEv2! So i had to change something. Very fast I found a very good alternative pfSense 2.4.4-p1, an Open Source Firewall which is also available on public Azure.
My Setup:
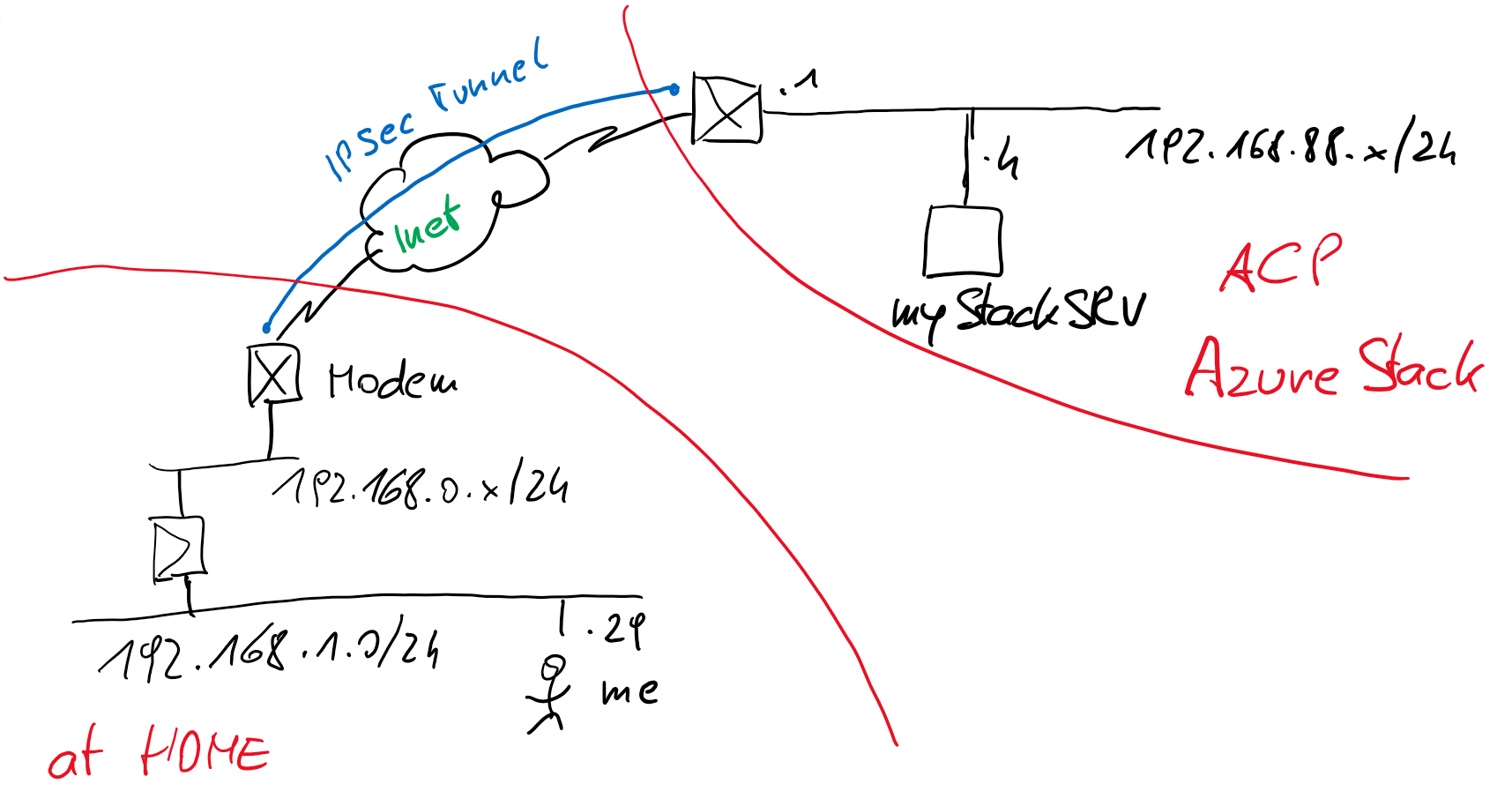
Let setup the Tunnel – Management Summary:
IPSec Phase 1 – IKEv2 – PSK – AES265 – SHA256 – DH Group 2 (1024bit) – lifetime 28800sec
IPSec Phase 2 – ESP – AES256-GCM – SHA512 – no PFS – lifetime 27000sec
the paramters are well documented here.
The IPSec Tunnel – Overview on Azure Stack
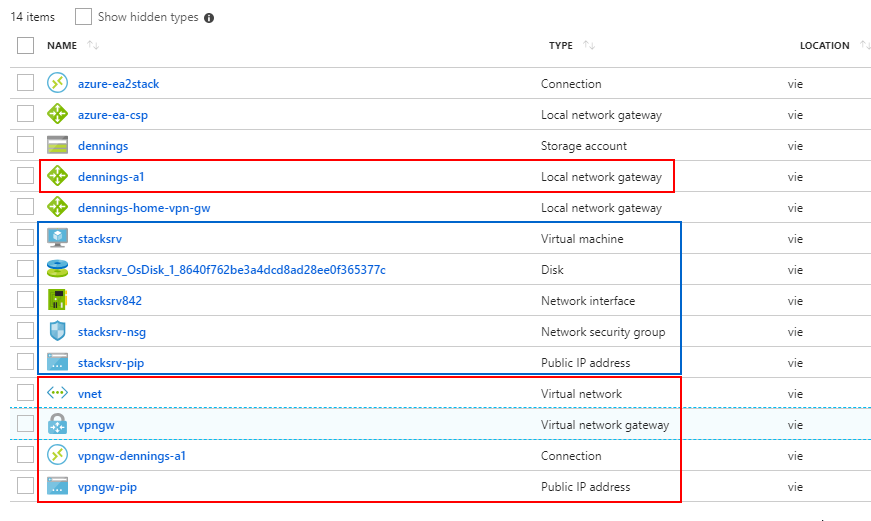
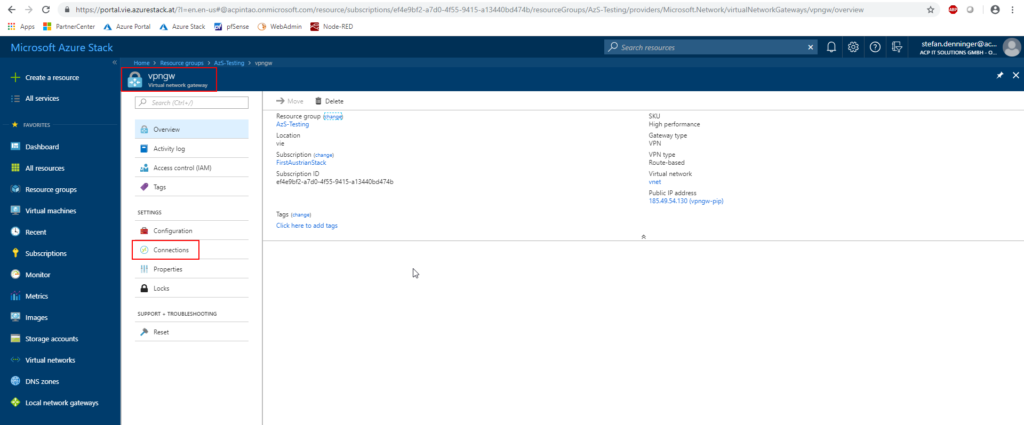
In the Management Portal you need the follwoing items:
- vNet – the remote Network
- VPN Gateway (the IPSec Gateway)
- public Ip Address (IP of the VPN Gateway)
- local Network Gateway (my Firewall at home)
- Connection (the PSK inbetween)
The IPSec Tunnel – Overview at the pfSense Firewall
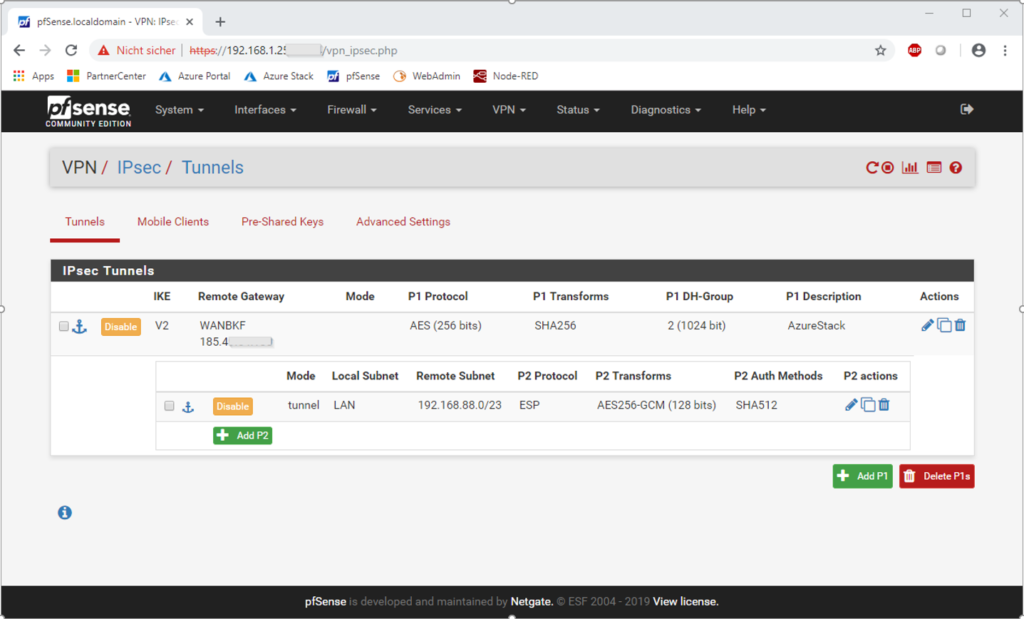
IPSec Phase 1 – IKEv2 – PSK – AES265 – SHA256 – DH Group 2 (1024bit) – lifetime 28800sec
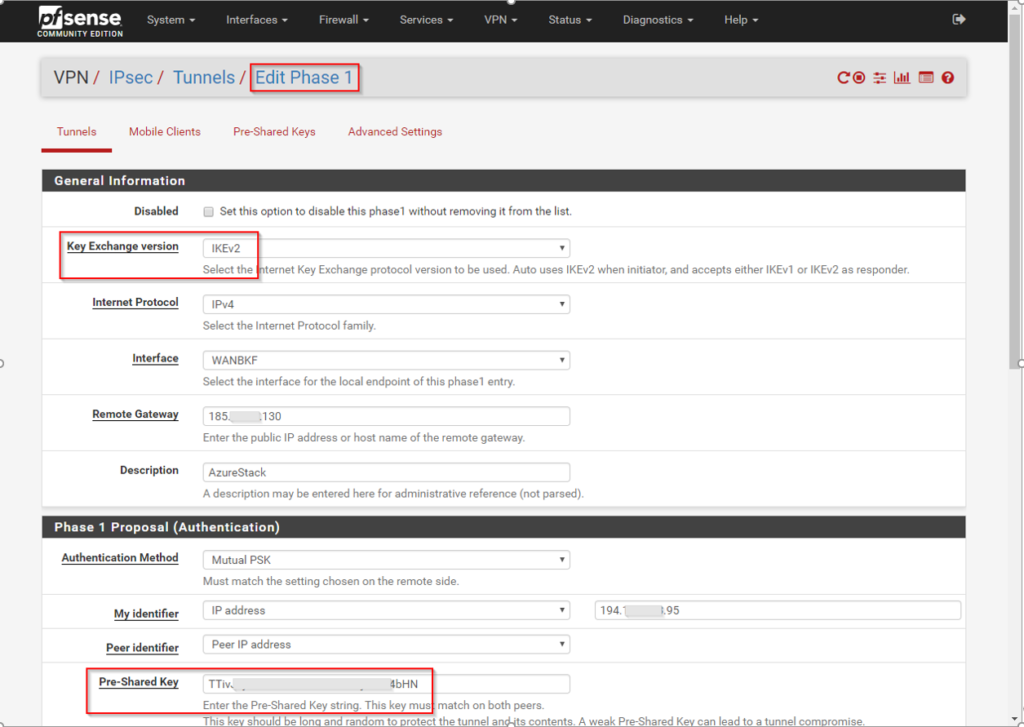
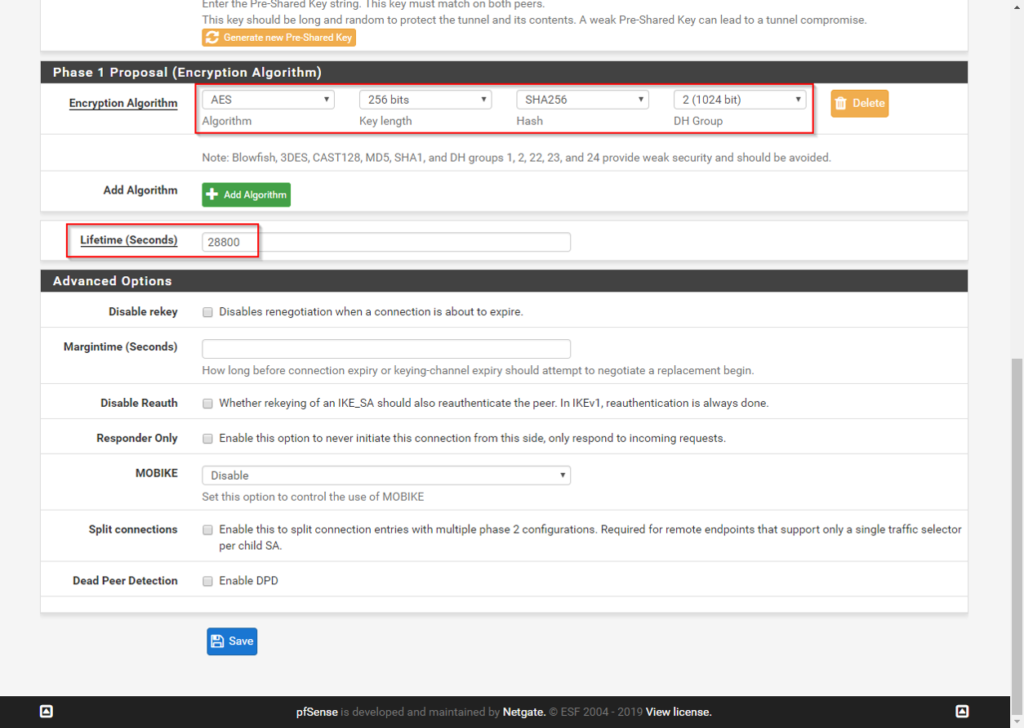
IPSec Phase 2 – ESP – AES256-GCM – SHA512 – no PFS – lifetime 27000sec
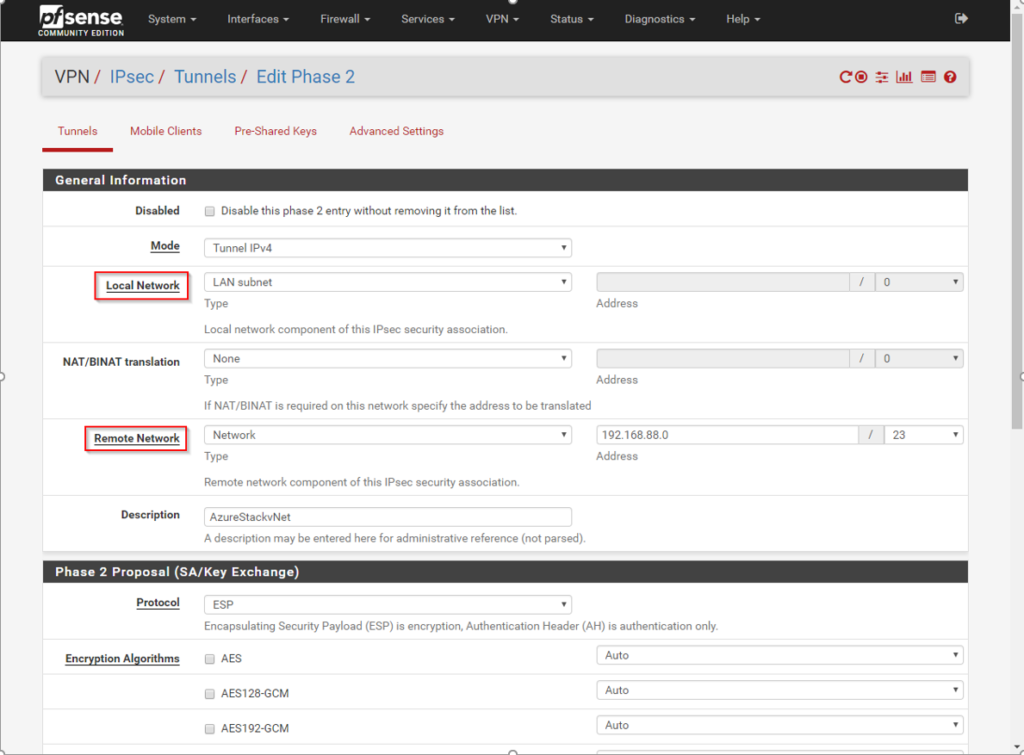
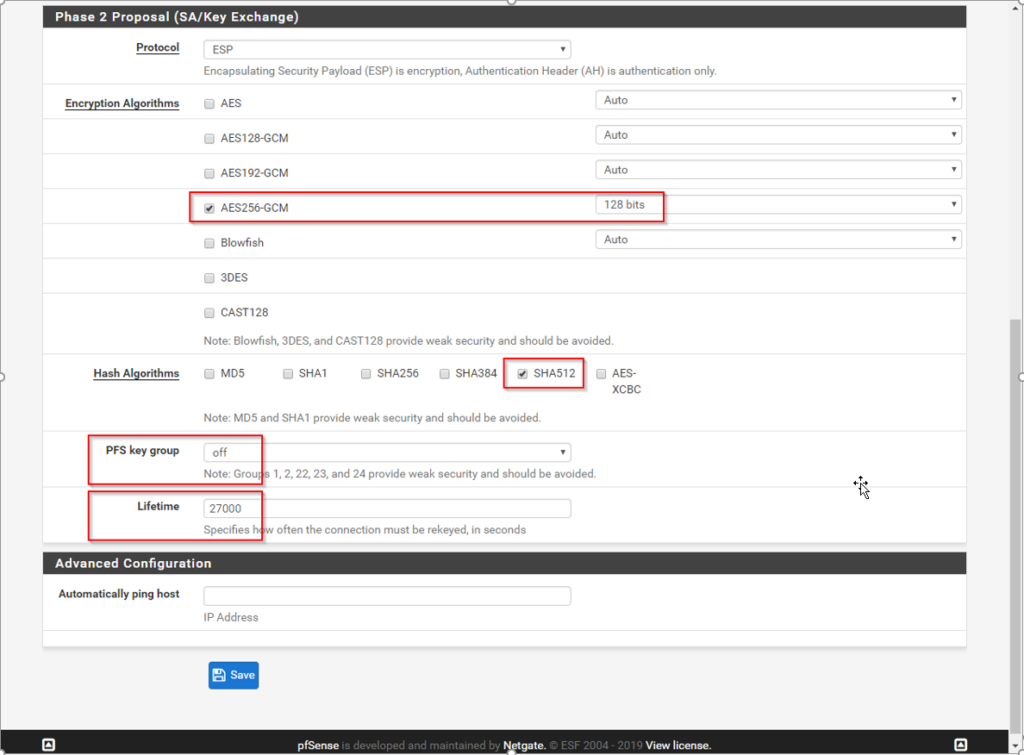
So, after setting up that parameters, the tunnel will come up and is doing well. It could be that you need to ping some host at that other site, so the tunnel starts to come up.
Showing the Status of the Tunnel:
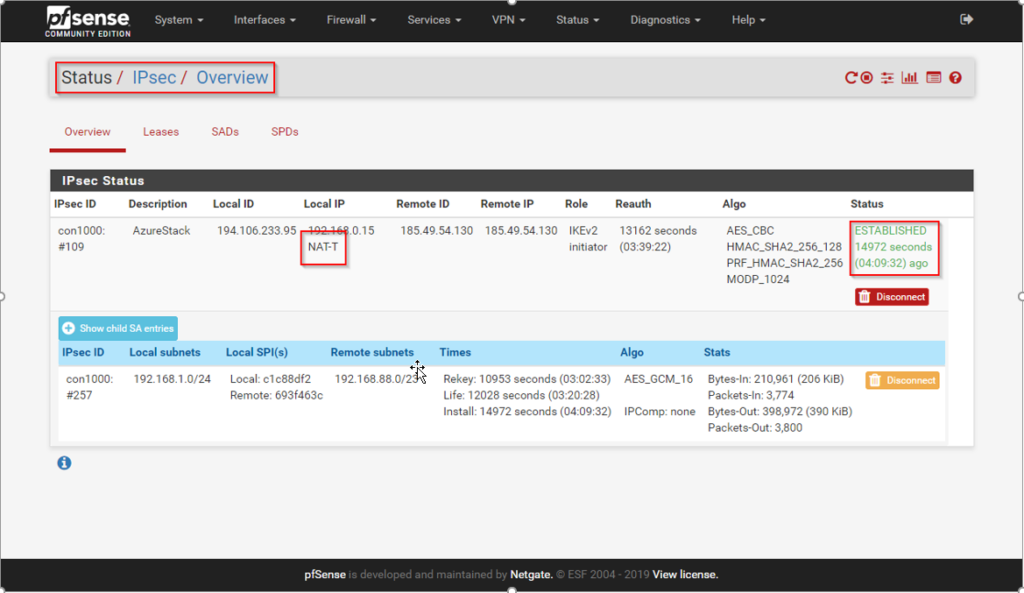
NAT-T: the IPSec IKEv2 Standard brings by default the possibility to support Traffic over a NAT Firewall. So, IKE uses udp/500 and the traffic runs over udp/4500. So, in my home I have a cable modem which forces me to do a NAT.
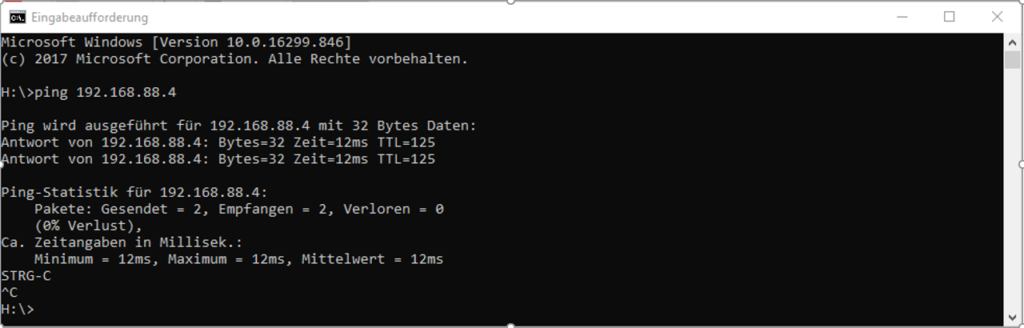
That’s it 😉
btw: it is well documented, but to see the real world makes you confident.
