Azure VPN w/ BGP to Fortigate w/ 2 ISP Uplinks
As a showed last time with mikrotik, there is a easy way to connect your OnPremises Infrastructure to your Azure vNet. But this time I show you how to do that with an Fortigate Firewall. Because this time there are some different setting because all vendors have their specials 😉
So let’s have a look what we have done because there are some different tasks and thinking of how vendors are getting the thing done. Many thanks to my college Johannes Kainz how was helping me to overcome the tricky things.
The different thing this time was the clustering an thus the one management intereface of the Fortigate system OnPremises. So there was no way to set two BGP Session to just one Azure VPN Gateway Management IP because the logical one firewall cluster need two differnt endpoints for its BGP peering address, so the result was an Azure active/active Gateway so that ends up in two public IP-Addresses but more important two internal Management IP-Addresses and so the Fortigate Firewall had two destination to connect. That’s it 😉 The Rest is just do it and straight forward.
The picture below show the lab setup where 2 different subsriptions where connected by vNet-Peering and brings you in mind that “global vNet Peering” is still a nice feature! So Addressspace (aka vNet) 10.10.4.0/22 lives in Central WestGermany Region which means Frankfurt. The main vNet 10.10.0.0/22 live in WestEurope which means Amsterdam which hostes the VPN-Gateway with the SKU VpnGw1 plus an additional Public IP Address. For Cost Perspective read futher down..
Hardware:
- Fortigate 60F in a Cluster for redunancy – FGT60F-7.0.6-FW-build0366
- Azure VPN Gateway VpnGw1 with BGP
- second public IP Address for active/active VPN Gateway
the WAN plan
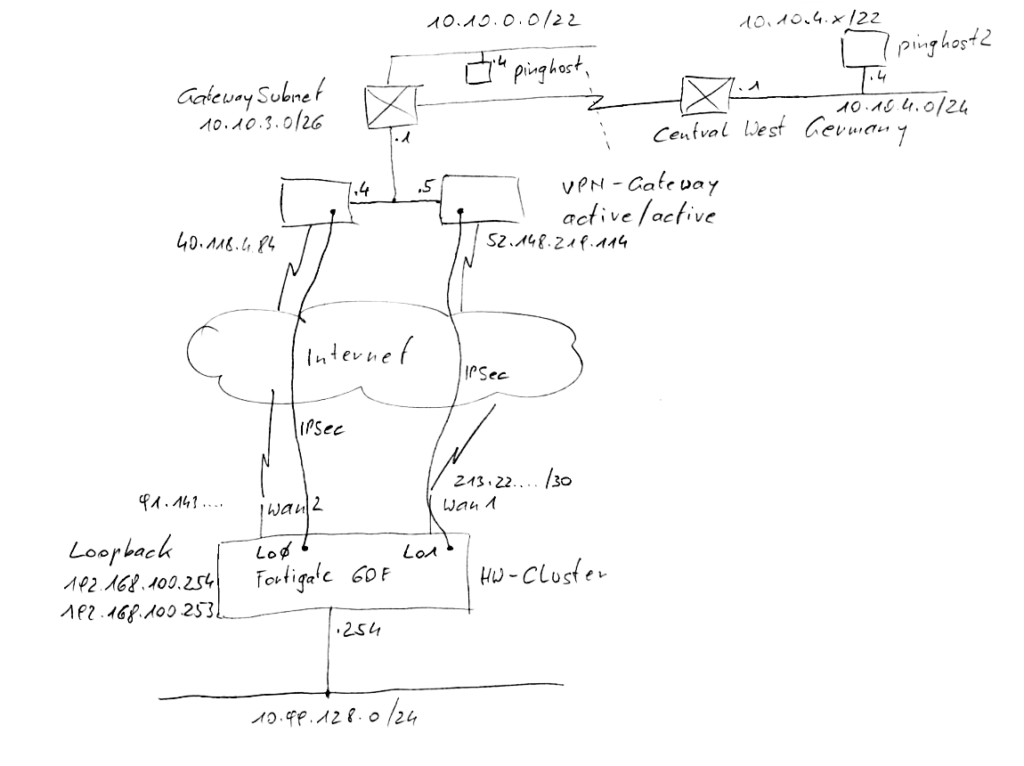
10.10.4.0/22 (Germany West) <–> 10.10.0.0/22 (Western Europe) <–> 10.99.128.0/24 (Feldbach city)
As you can see there is a config for redunand VPN connection to your Azure vNet. For the showcase I did a second vNet in a different reagion just to show that “global vNet Peering” is possible and also part of perfect connectivity.
Lets start with the part for the Fortigate Firewall and how to setup the IPSec Tunnel with BGP Routing. I just show the relevant parts. Someone doing that should be able to setup the rest of the firewall so that internet access is possible…
There are some parts of course:
- the config at the OnPremises with Fortigate
- the config part in the cloud – Azure VPN Gateway
- the result
- the cost estimate of the solution
The Fortigate part
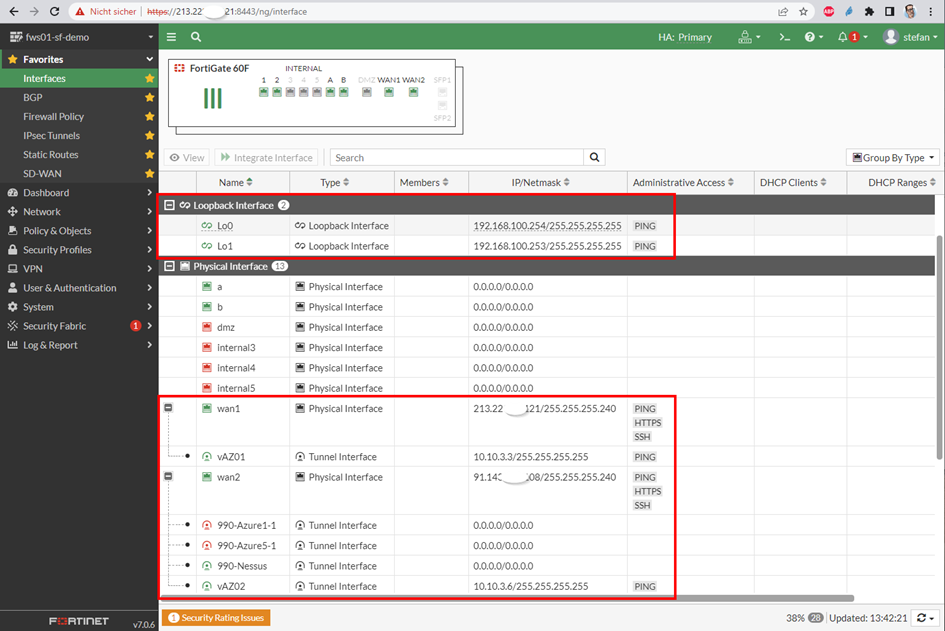
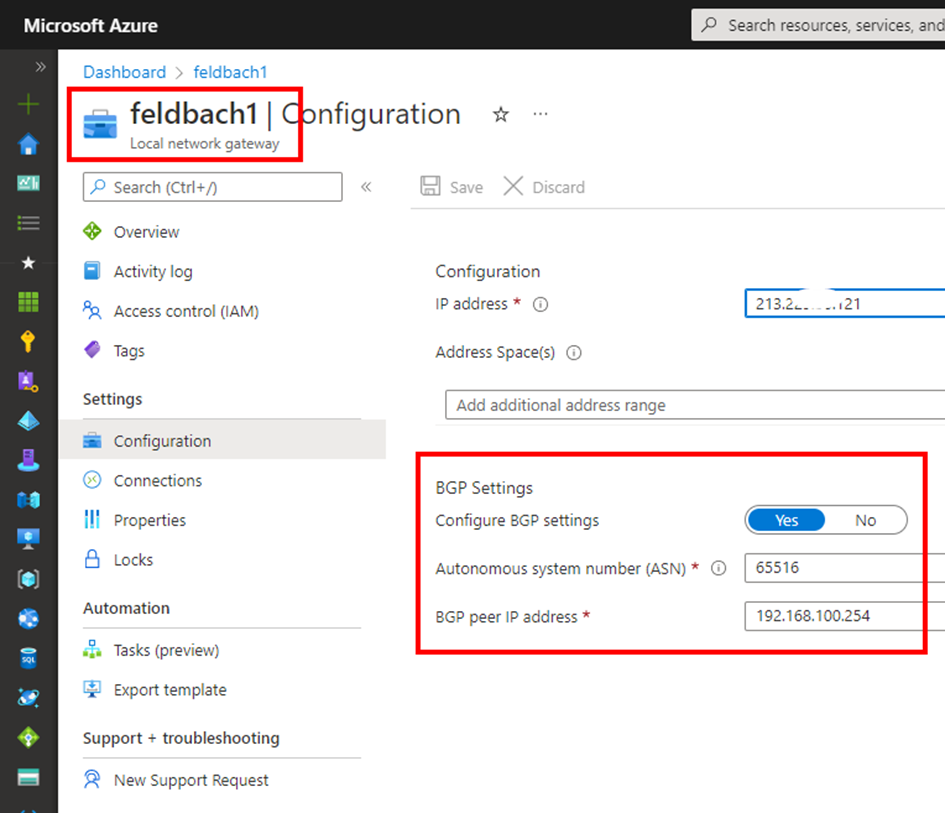
The new thing here is the second Loopback Address because we need two separate BGP Session or BGP Destinations to the Azure VPN Gateway. Because of that we needed the active/active Azure VPN Gateway because this brings us access to the second Gateway Instance and a seconde BGP Peering address!
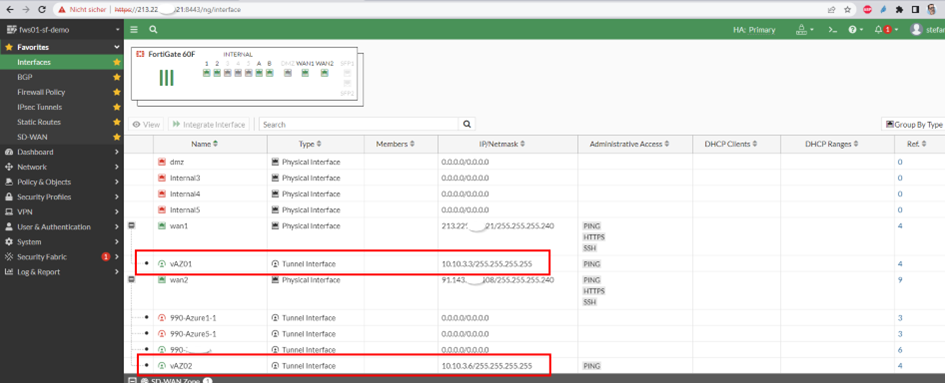
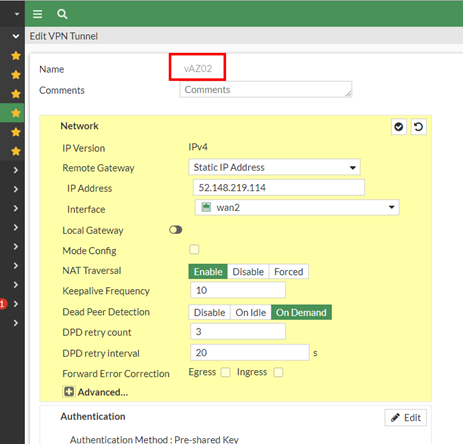
of course 2 different IPSec Interfaces for the 2 tunnels, IP Addresses are not interested
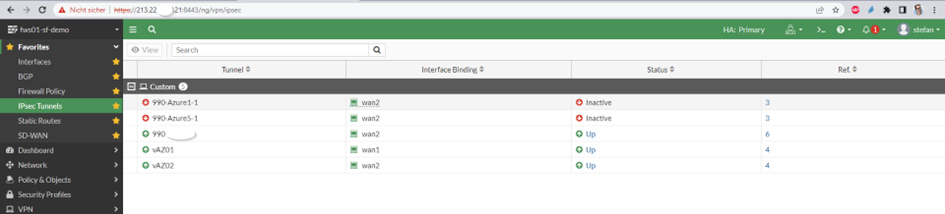
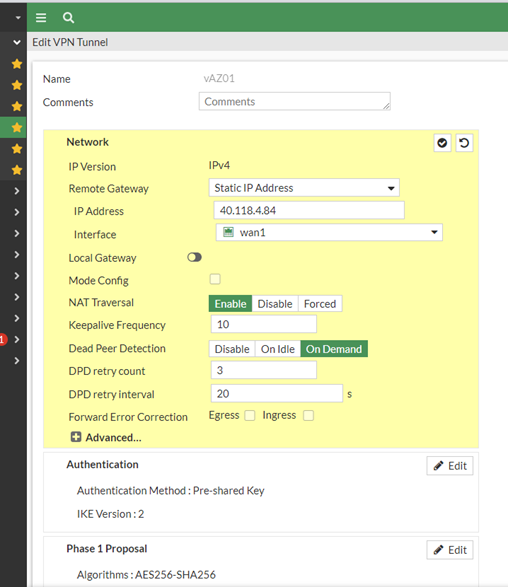
The IPSec Setting are well known but i put it here – please note that there are of course 2 Tunnels:
We tried to put the most secure settings which are working! So take that and its working…
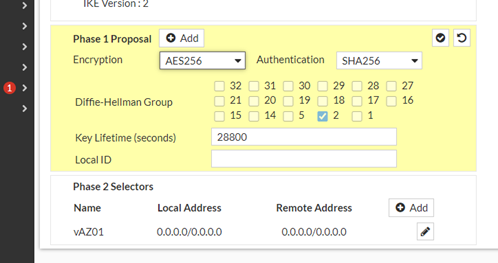
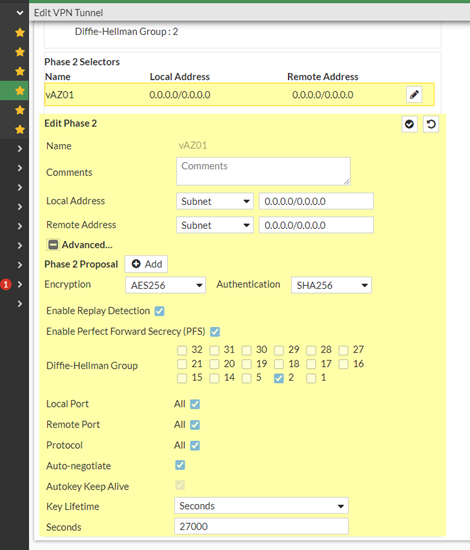
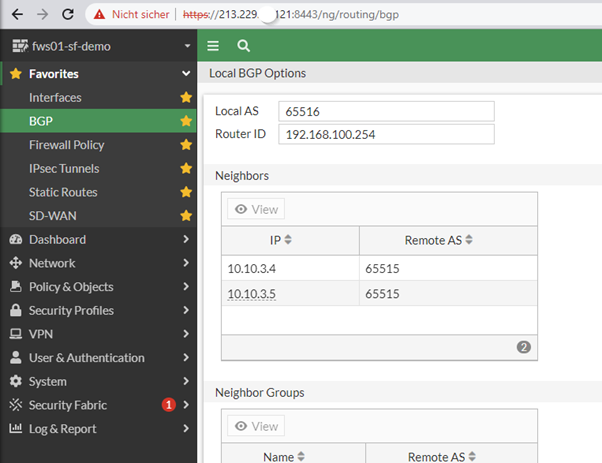
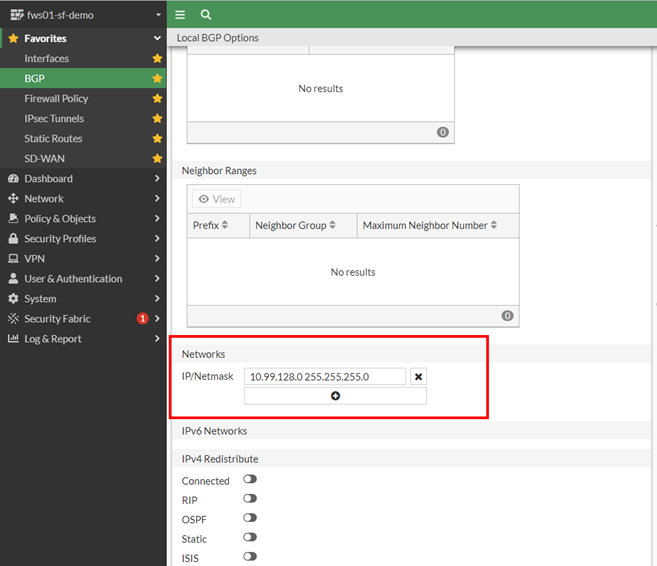
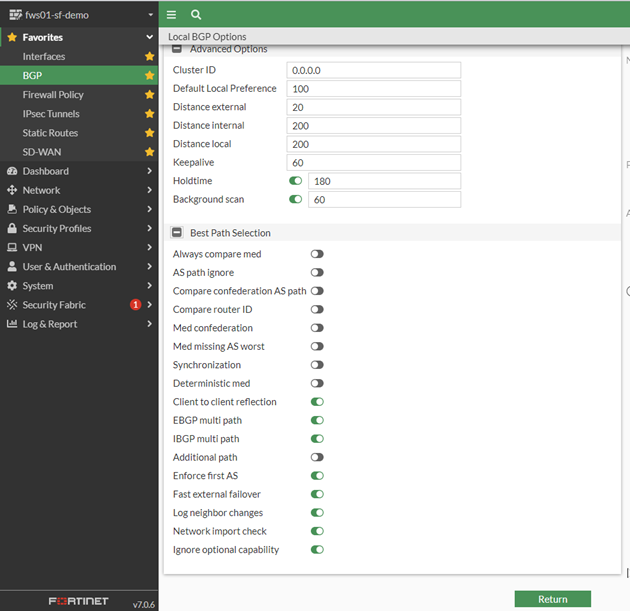
do some BGP stuff
now some BGP Settings. If you are new to Routing: BGP is the most common routing protocol because the whole Internet is based on it. For internal routing it is quite new. BGP Session are 1:1 session based on tcp/179 so, source and destination router must be reachable by static routes which is done by the firewall and Azure gateway automatic.
lets do the Azure part
Here are some steps you have to do on Azure:
Add an vNet with your desired IP Range here in my case it is 10.10.0.0/22 with some Subnets in the region of West Europe… Just as showcase i added another vNet in a different Azure Region “Gemany West Central” just to show that this is easy going and possible. The feature is called vNet-Peering within an region and Global vNet Peering cross Regions. Here it is 10.10.40/22 in Frankfurt.
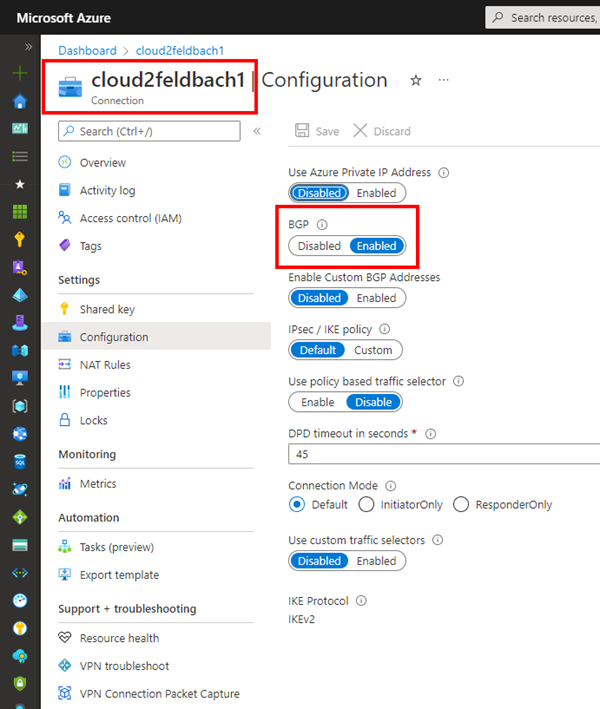
So add an vNet 10.10.0.0/22 and add an VPN Gateway with active/activ enabled!
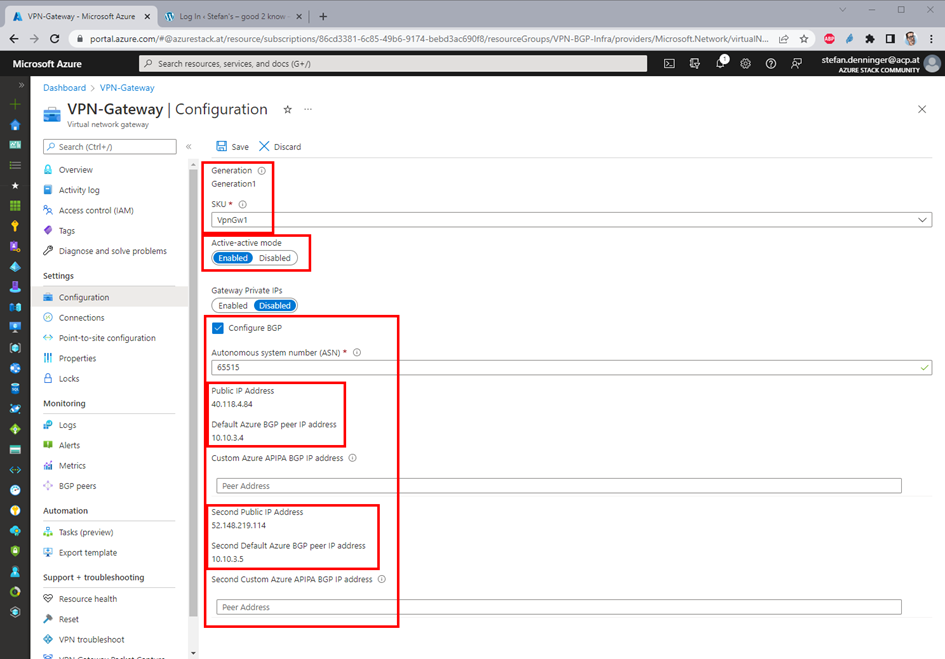
I the screenshot above you can see the two public IP Addresses to connect from OnPremises but more important the two BGP peering addresses which has the VPN Gateway Cluster on Azure to connect within the IPSec Tunnel for the BGP Sessions.
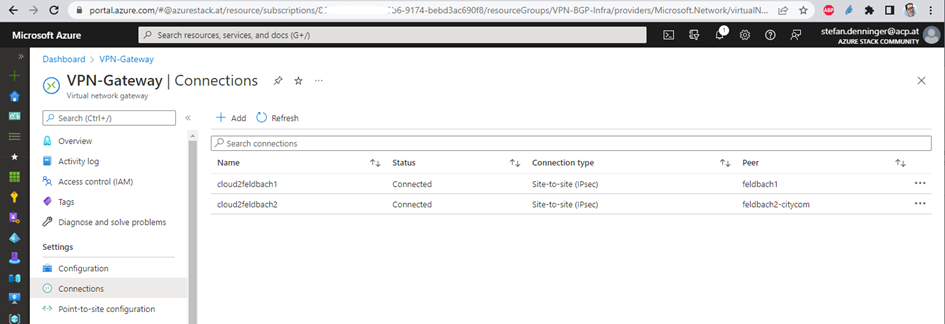
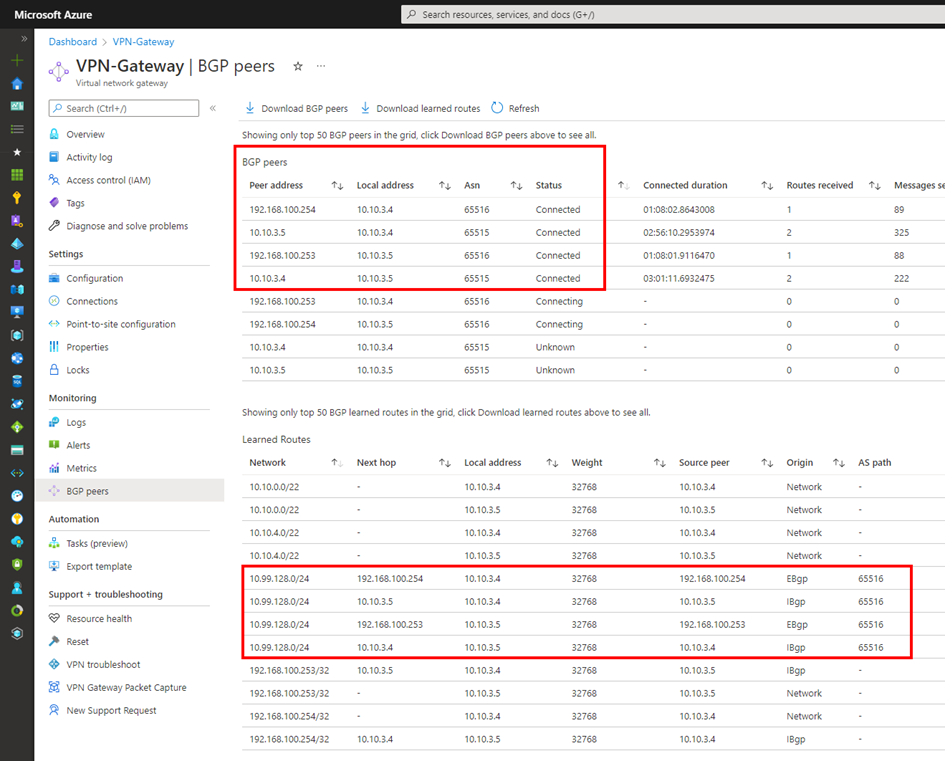
the result
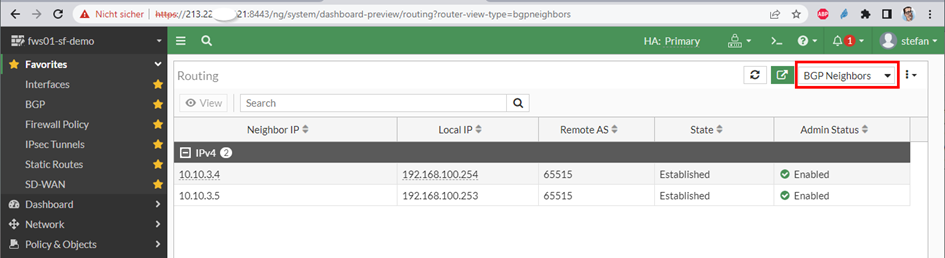
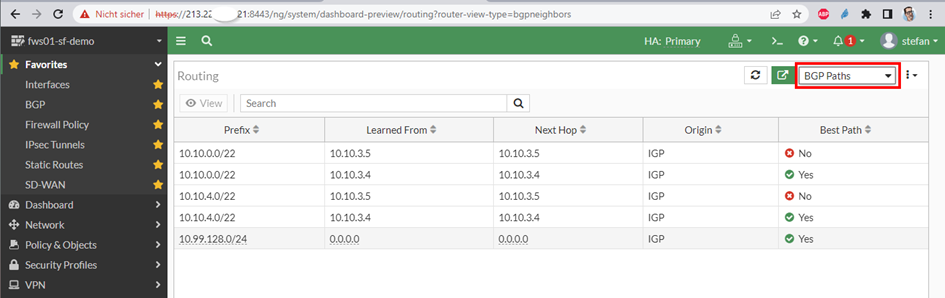
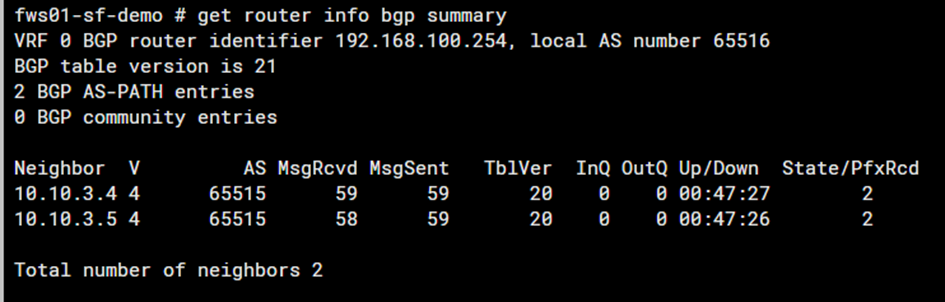
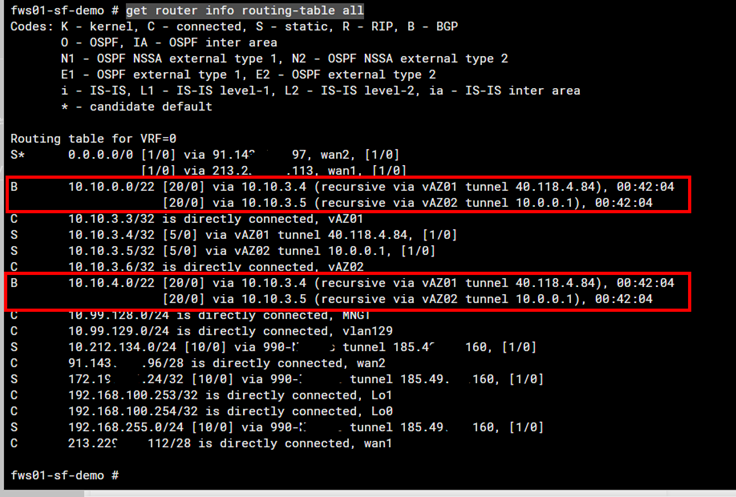
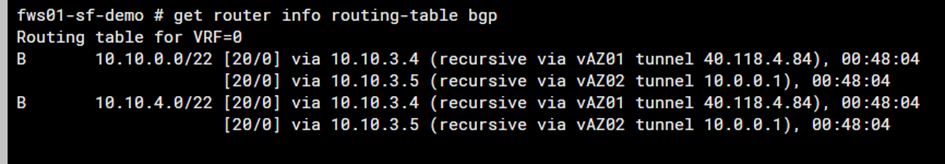
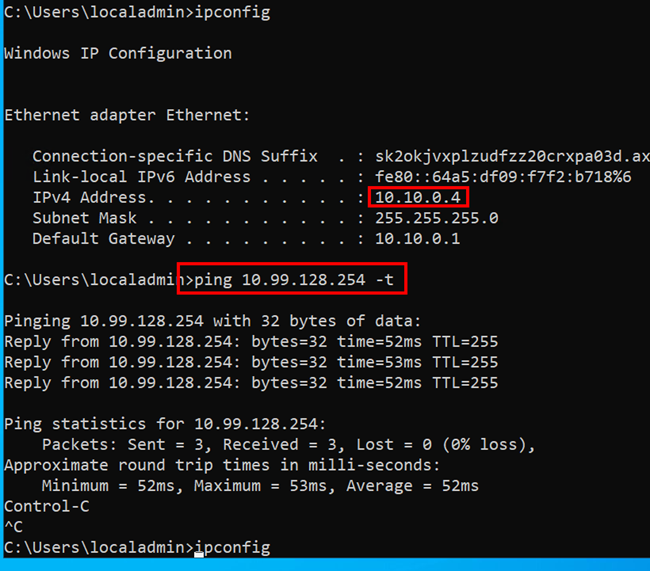

as always – when you do things right – it works 😉
Cost Perspective
The greatest myth in cloud: Costs 😉
I think that is really wrong because there is nothing which is more going in detail than costs. I kept the shown infrastucture running for a while so I show you the very sure cost from ervery day runrate.
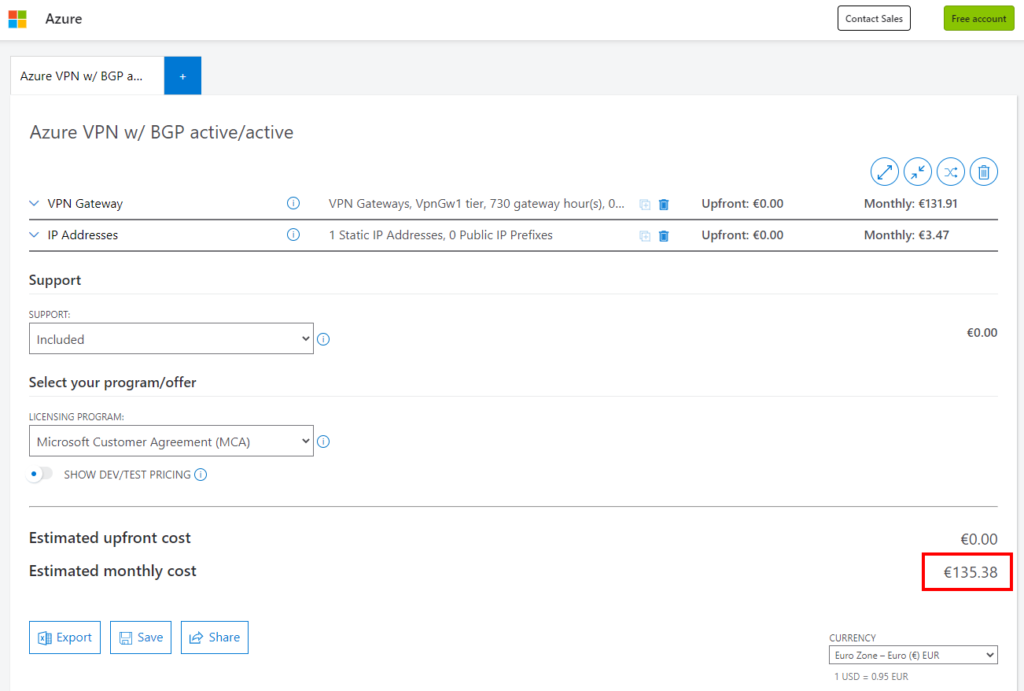
sorry quite long but useful…
That’s all folks!
