Route based IPSec to mikrotik RouterOS7 with BGP
There are many instructions for miktrotik, but few that work. Precisely because a lot has changed with Router OS v7, I would like to show a few variants here:
- “simple” IPsec tunnels (I show later)
- Route-based IPSec tunnels with BGP
so lets start with the tricky:
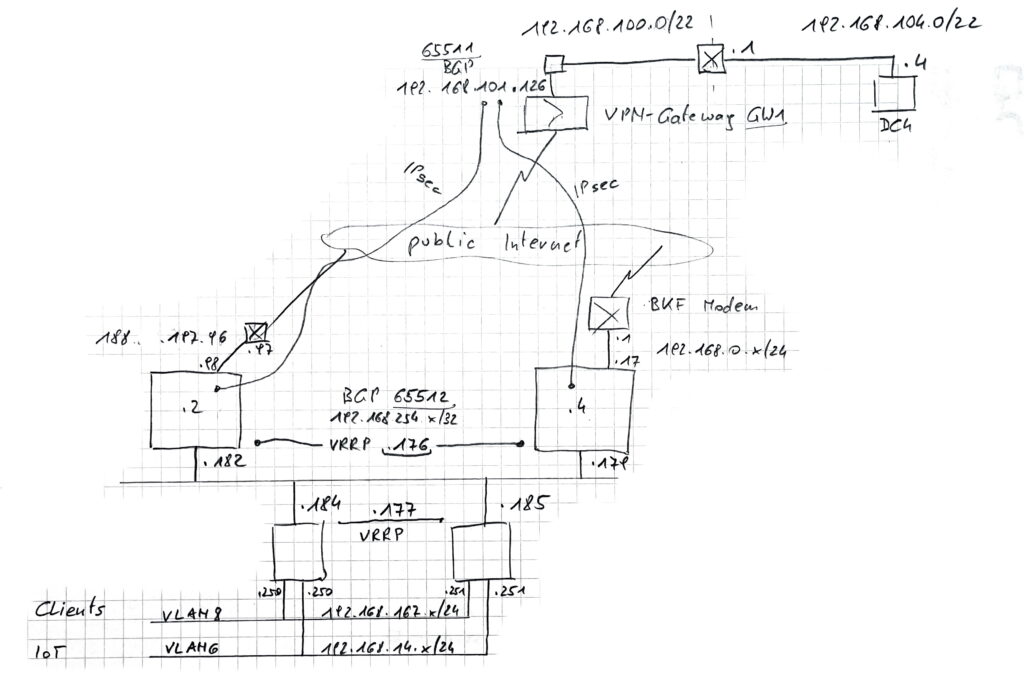
I have 2 ISPs with 2 public IP-addresses, right. So to make the connection redundant we need also a routing protocol to make the paths automatic switching over when one way fails. In Azure we have to use BGP because there is just that option.
the WAN Plan

the Azure side
so I have 2 vNets because of 2 Subscriptions. Subscriptions are not connected by default, so I had to connect them by usng vNet-Peering. Then my vNet apo-vnet (192.168.104.0/22) and my second vNet infra-vnet (192.168.100.0/22) is connected and the apo-vnet is using and sharing the VPN-Gateway, so there is just one VPN-Gateway needed.
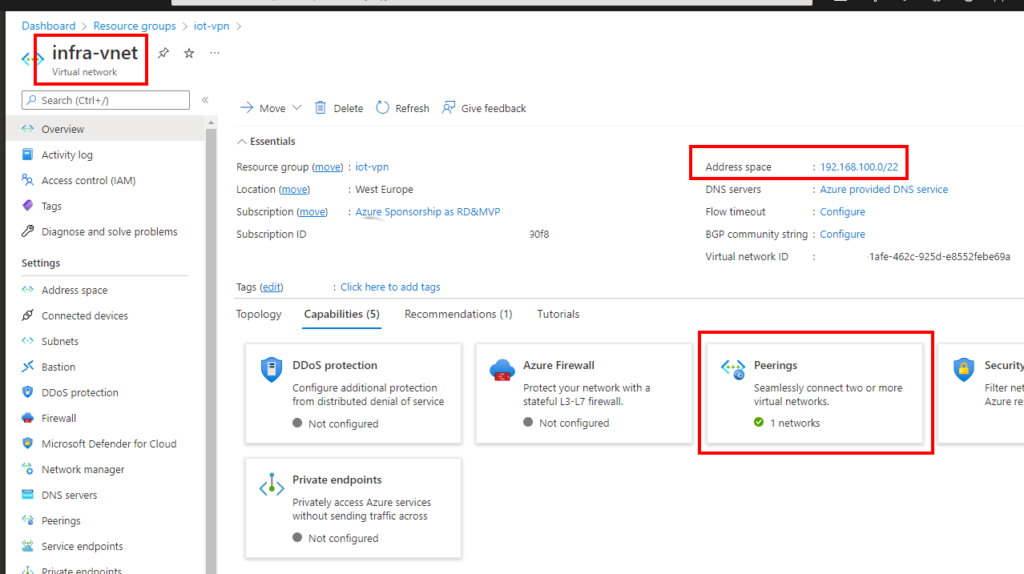
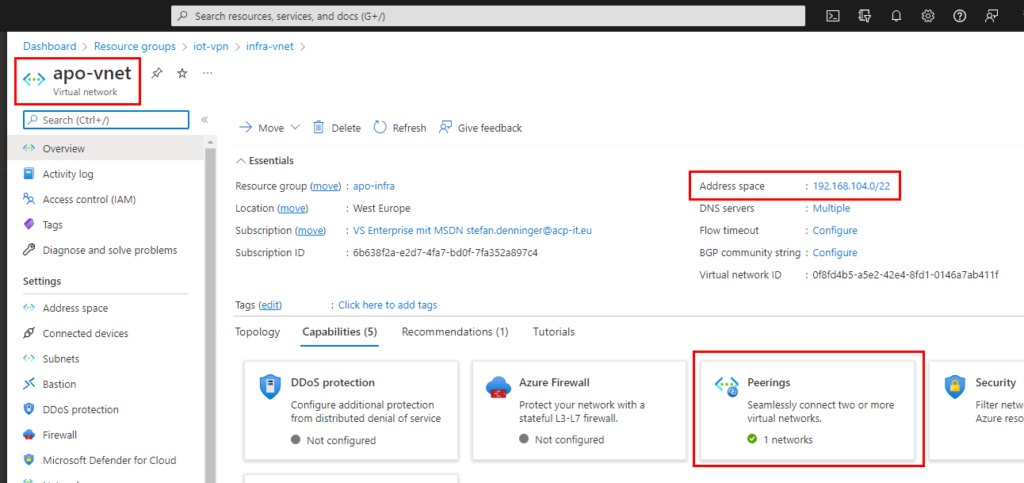
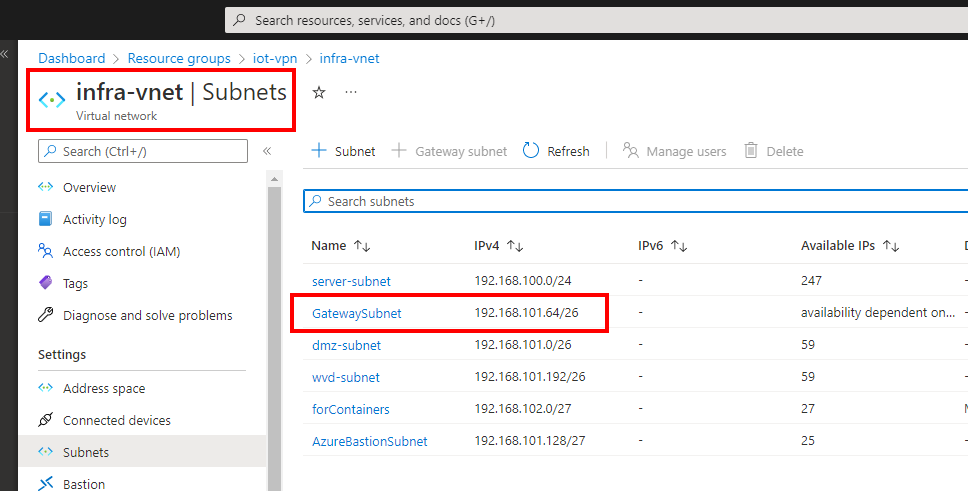
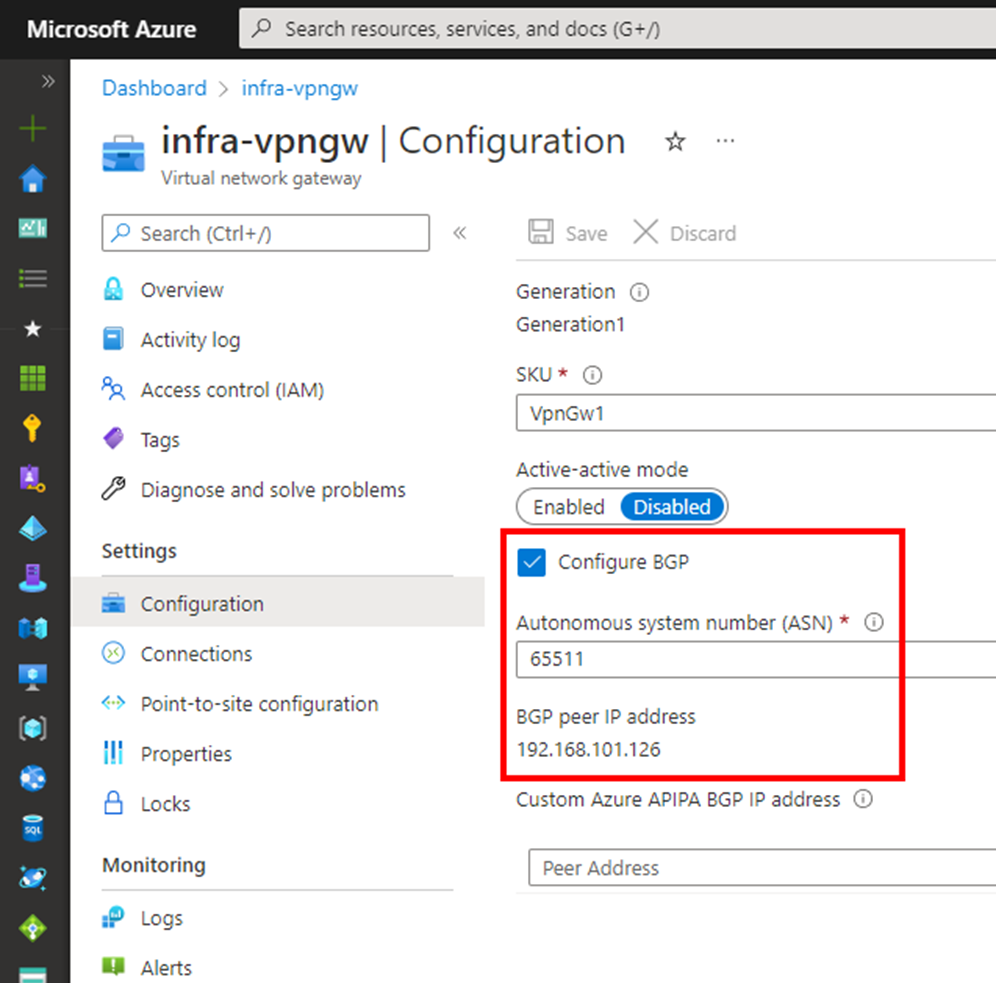
the VPN Gateway is a “normal VpnGw1 SKU which is for most of the use-cases fully enough. The BGP Feature is built in at no additional costs.
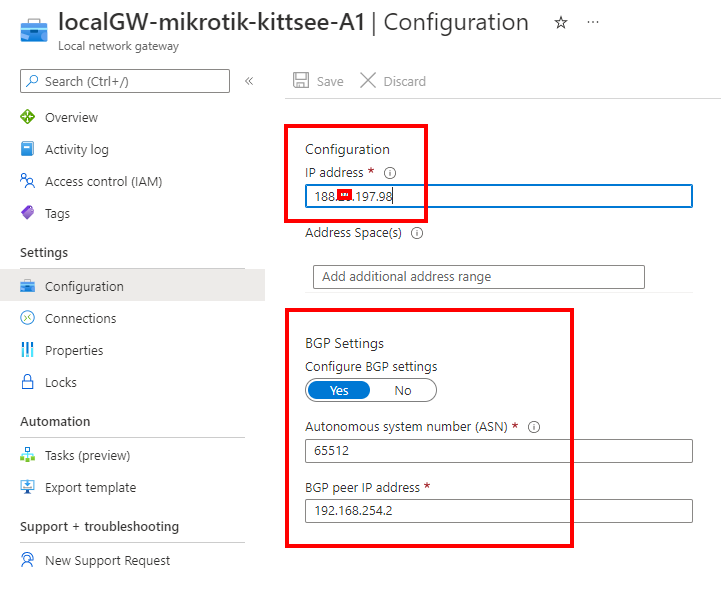
the mikrotik Side – aka On-Prem
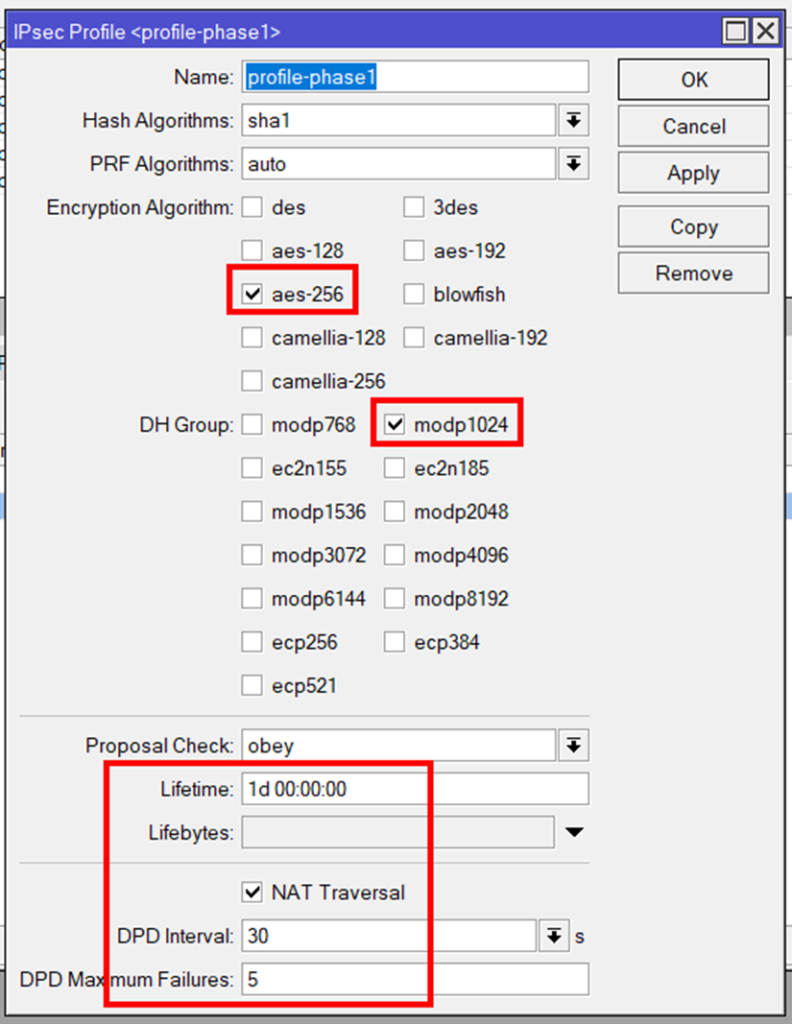
TL;DR: the IPSec settings in the mikrotik RouterOS v7 – I am currently using 7.3.1:
Phase1: aes-256, sha1 or sha256, modp1024, lifetime 07:30:00 7h30=27000sec, just in my case NAT-Traversal because i am behind a NAT-Router so udp 500/4500 is usedfor the connection.
dead-peer-detection is set to 30sec, so maximum recognition is 5×30 = 150sec.
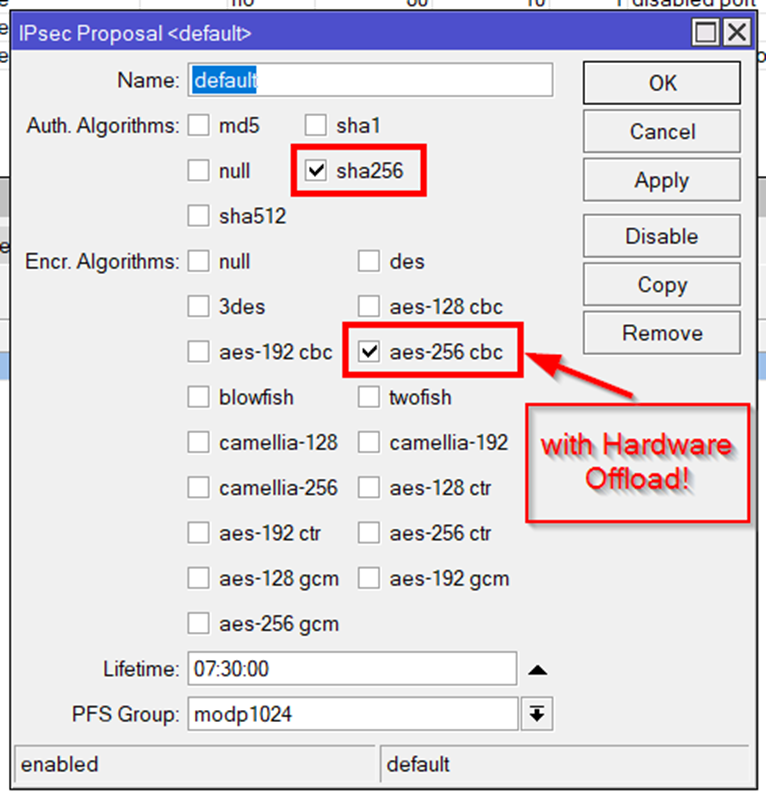
Phase2: aes256 cbc (only that is in hardware!), sha256, lifetime 07:30:00 and PFS modp1024.
other combinations may also work but are not tested.

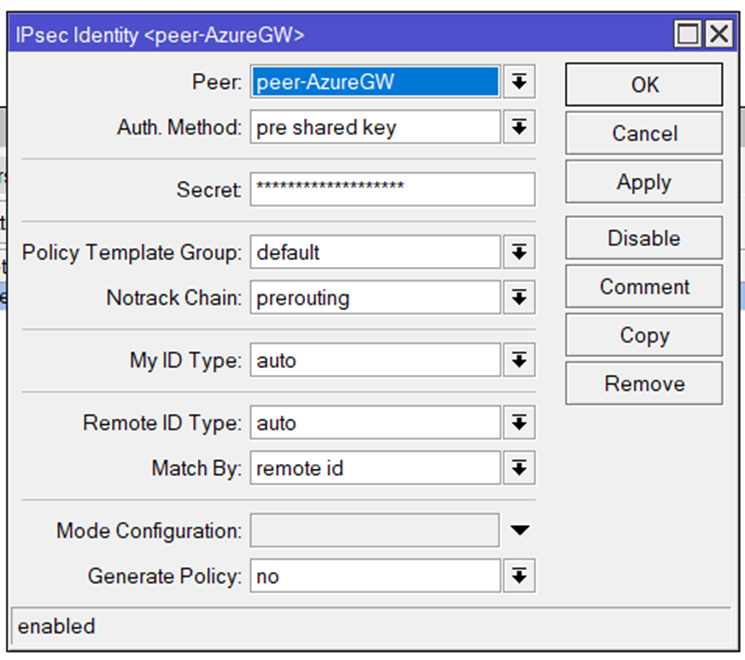
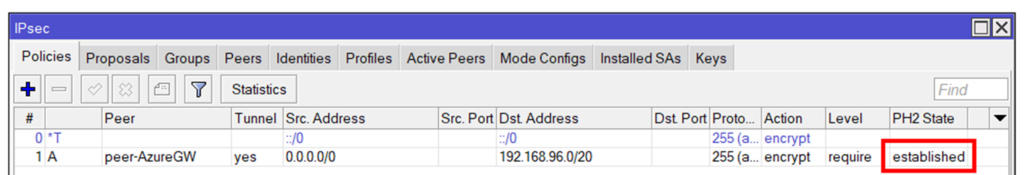
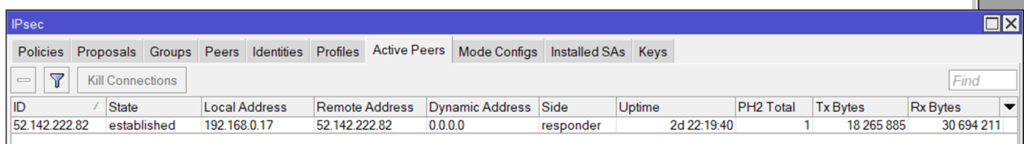
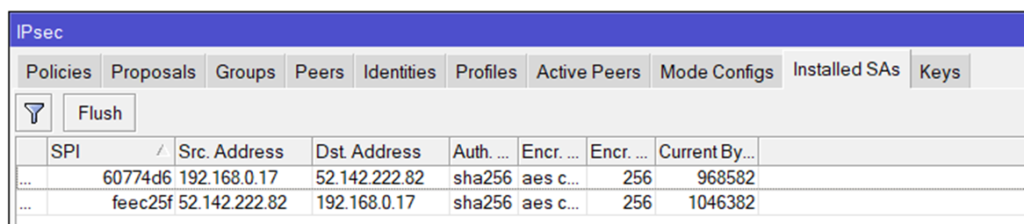
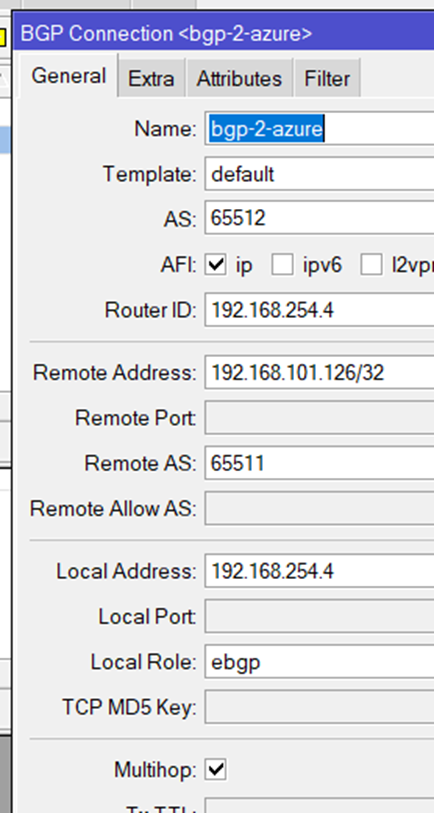
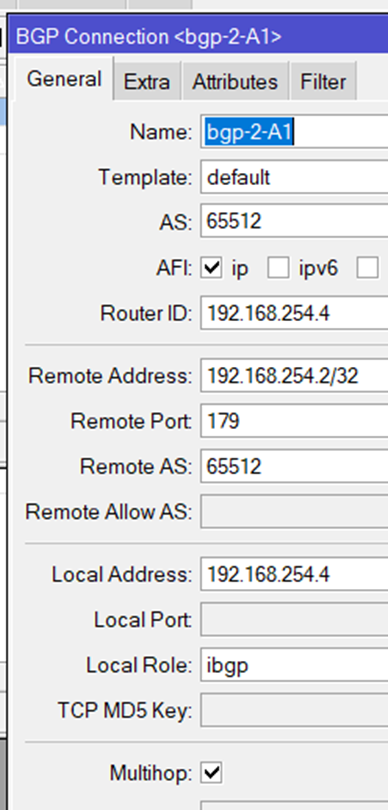
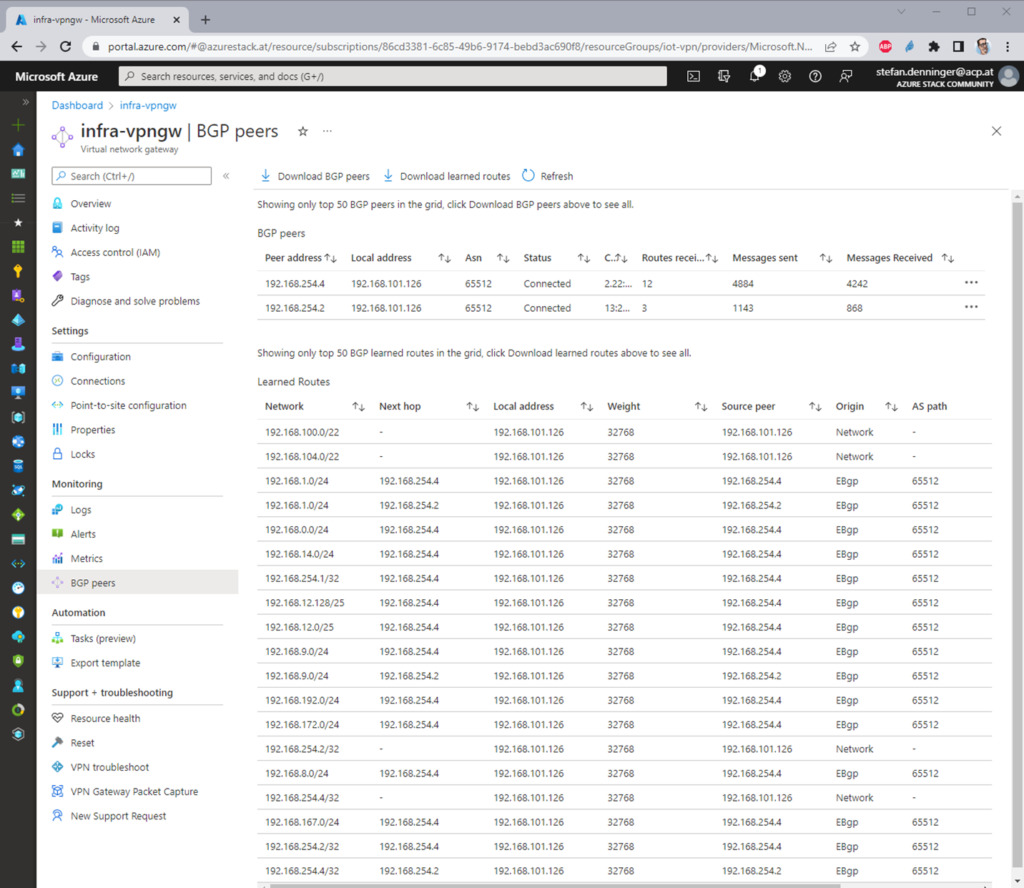
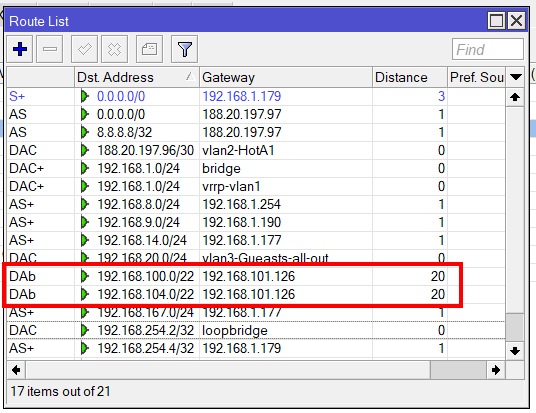
the BGP Routing part – On-Prem
because we are routing between loopback-Adresses which are always online, we are creating socalled loopback-Interfaces. Giving them a fixed non-overlapping IP-Address (192.168.254.2 and 192.168.254.4) and set a static route to the other side.
the route to the Azure BGP Peer (192.168.101.126) is not needed because the default route show the direction.
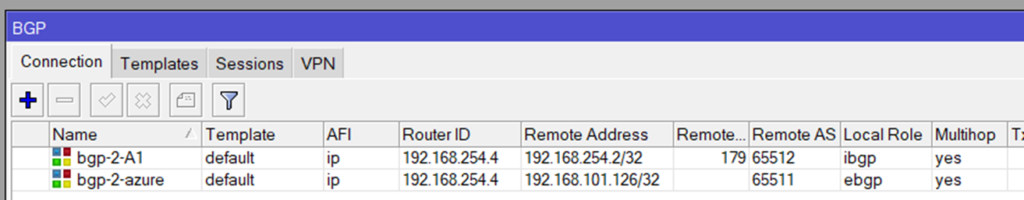
done 😉
ask my on twitter… @sdenninger