Site 2 Site VPN FortiGate to Azure Stack
Connecting Azure Stack to my FortiGate Firewall
I wanted to connect my new local Firewall to my Azure Stack vNet. As I described later this year I did it with my old firewall which was a virtual pfSense Firewall. It was very good to learn the real parameters and to proof that against a commercial product.
Things to configure:
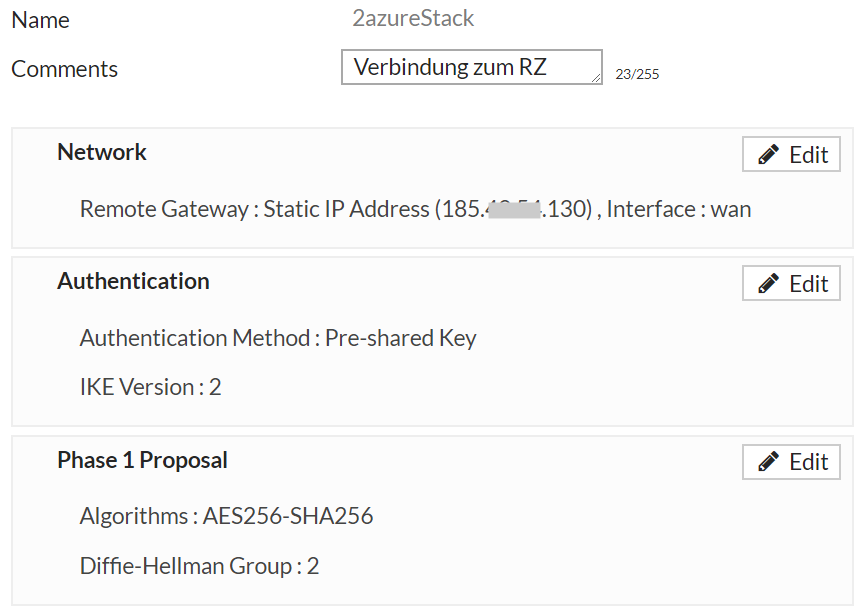
- IP Sec Tunnel Phase I – AES256-SHA256, DH Group 2, 28800 Timeout
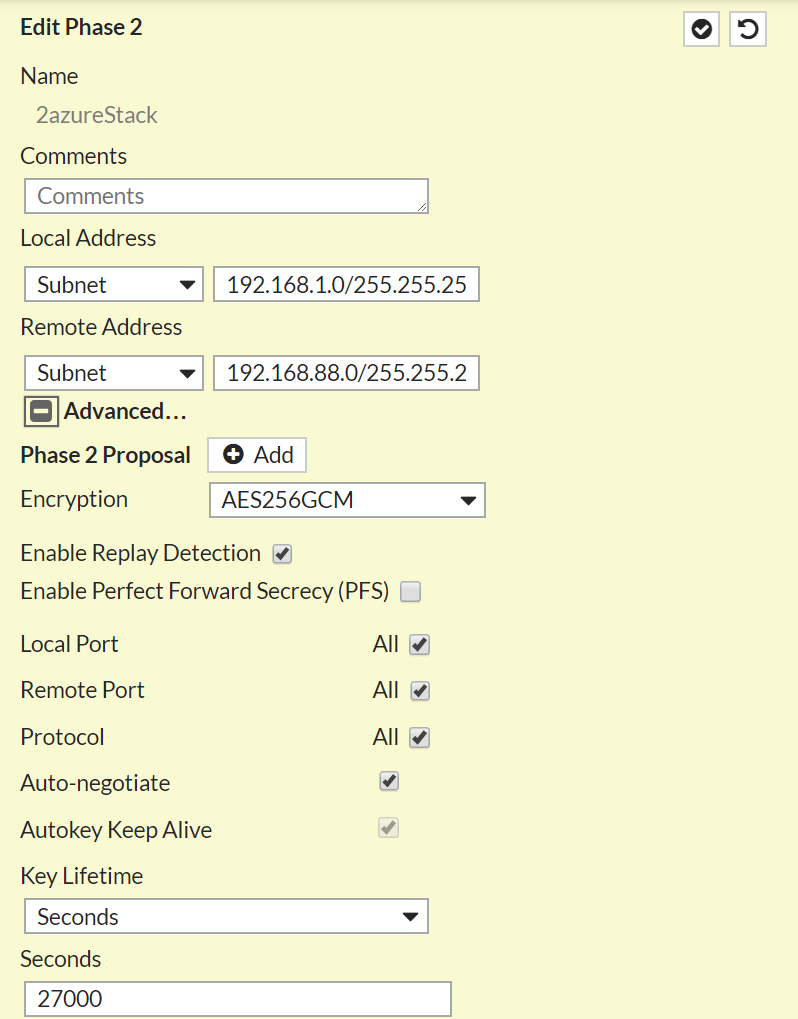
- IPSec Tunnel Phase II – AES256GCM, AutoNeg on, 27000 Timeout
- IP Policy
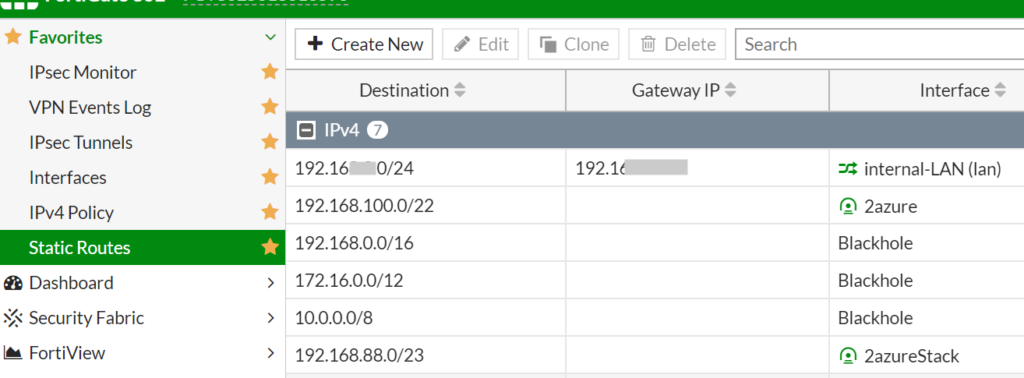
- Static Route
Here are the tunnels configured:
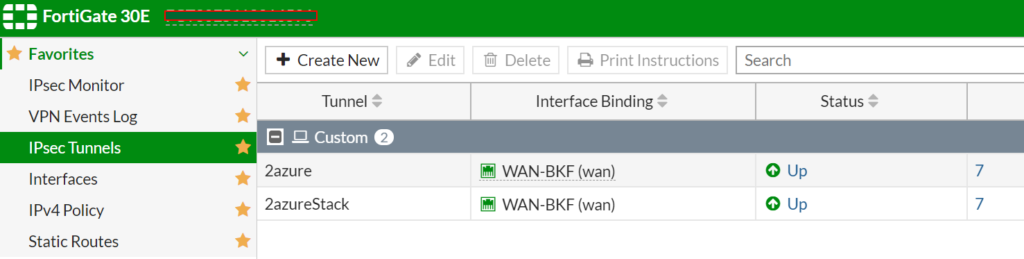
Phase I:
Phase II:
The IPv4 Policy to make it easy – Allow ALL 😉
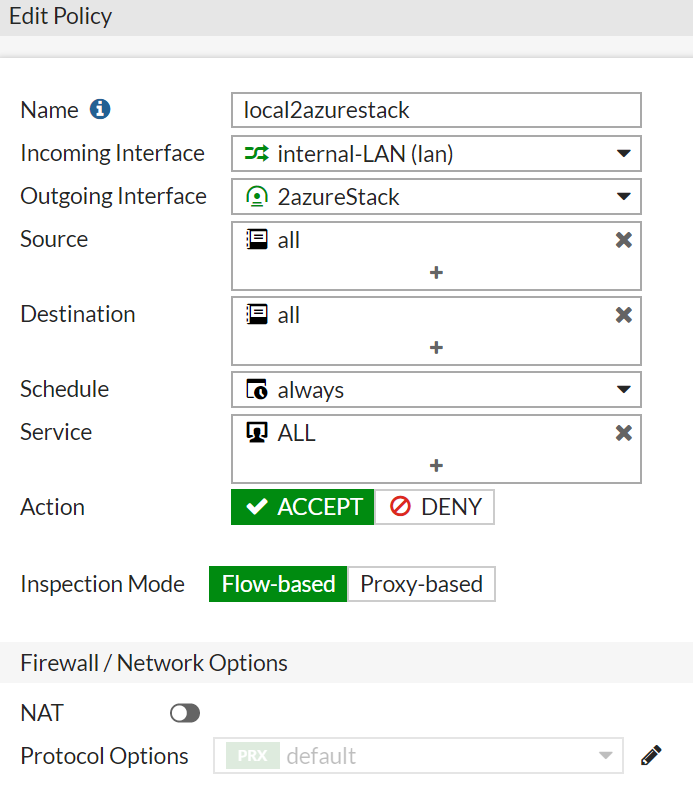
And lets make a static route to the Azure Stack vNet:
In the IPSec Monitor you can see your success 😉
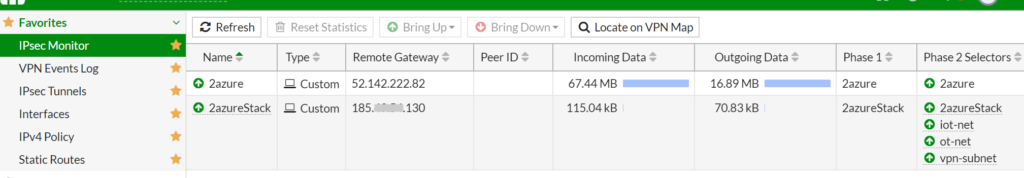
Here is the template of the Config and the VPN Settings in Phase I and Phase II:
config vpn ipsec phase1-interface
edit "VPN-AzureStack"
set interface "wan1"
set ike-version 2
set keylife 28800
set peertype any
set proposal aes256-sha256
set dhgrp 2
set remote-gw xxx.xxx.xxx.xxx
set psksecret ENC xxxxxxx
next
end
config vpn ipsec phase2-interface
edit "VPN-AzureStack01"
set phase1name "VPN-AzureStack"
set proposal aes256gcm
set pfs disable
set auto-negotiate enable
set keylifeseconds 27000
set src-subnet 192.168.x.0 255.255.255.0
set dst-subnet 192.168.y.0 255.255.255.0
next
end
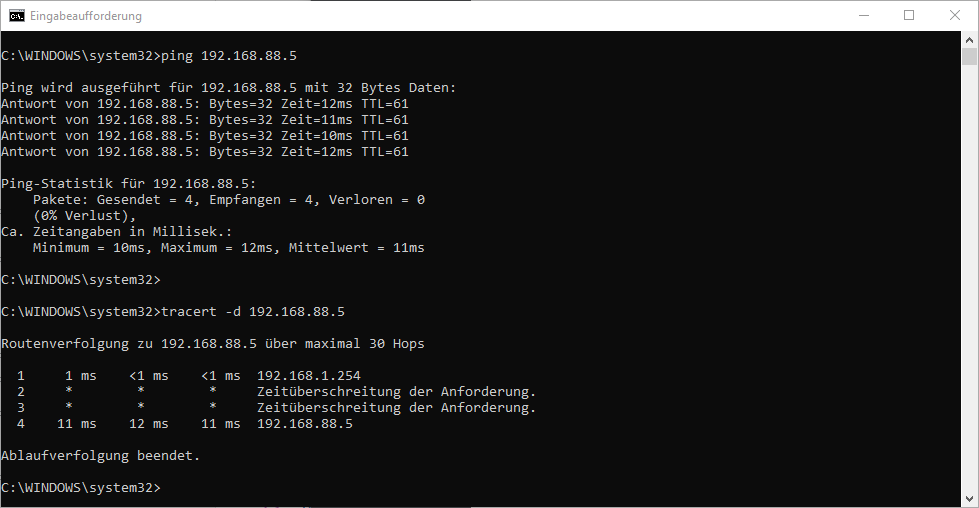
DONE 😉